Abstract
This paper examines the challenges posed by data breaches in the digital age, focusing on the legal and ethical implications. Using the recent Volkswagen (VW) data breach case as a primary example, it explores the broader implications for data protection, cybersecurity, and trust in technology-driven businesses. The paper also discusses steps organizations must take to mitigate risks and comply with global data protection laws.
1. Introduction
In an era where data-driven technologies permeate every aspect of modern life, the security and privacy of sensitive information have become paramount concerns. With the increasing reliance on digital ecosystems, particularly in connected technologies such as electric vehicles (EVs), data breaches have emerged as critical challenges. These breaches not only expose organizations to significant financial and legal repercussions but also undermine consumer trust and adoption of innovative technologies. A recent case that underscores these vulnerabilities is the Volkswagen (VW) data breach, where sensitive information of 800,000 EV owners was exposed due to mismanagement of cloud storage credentials. This incident highlights the broader implications of cybersecurity lapses in the automotive sector, where data over-collection and inadequate protections amplify risks.
Despite regulatory frameworks such as the General Data Protection Regulation (GDPR), which mandate stringent data protection measures, lapses like those seen in the VW breach demonstrate ongoing gaps in implementation. Insecure storage of location data, user credentials, and personal details represents a growing privacy nightmare for consumers, particularly in industries heavily dependent on interconnected systems. By examining this breach and similar incidents, this paper seeks to explore the intersections of cyber law, ethical responsibilities, and technical solutions to enhance data security and foster consumer trust in the digital age.
2. Background: The Volkswagen Data Breach
In December 2024, Volkswagen Group faced a significant cybersecurity incident, exposing the sensitive personal data of approximately 800,000 electric vehicle (EV) owners across its brands, including Volkswagen, Audi, Seat, and Skoda. This breach,
attributed to a misconfigured Amazon Web Services (AWS) cloud storage system managed by VW’s software subsidiary Cariad, left unencrypted data publicly accessible for months. The exposed information included user names, email addresses, phone numbers, physical addresses, and precise location data for 460,000 vehicles. Particularly alarming was the inclusion of location information with
accuracy to within 10 centimeters, enabling insights into users’ daily routines, such as home and work locations. Affected individuals included high-profile stakeholders, such as politicians and law enforcement officials in Germany, as well as car owners in several European countries. The breach was discovered by the Chaos Computer Club (CCC), a renowned ethical hacking organization, which identified vulnerabilities such as unprotected heap dumps in the backend system, exposing active AWS credentials. This oversight enabled unauthorized access to APIs, allowing potential misuse of user data. Although Volkswagen asserted that there was no evidence of malicious exploitation, the lack of encryption and poor data governance highlighted severe lapses in compliance with GDPR regulations. These failures not only exposed users to privacy risks but also posed significant reputational damage to Volkswagen, already recovering from previous controversies such as the Diesel gate scandal. The incident underscores broader concerns about the security of connected car ecosystems and raises questions about the ethical collection and retention of user data.
3. Legal and Ethical Implications
The Volkswagen (VW) data breach highlights a series of legal and ethical challenges that underscore the need for stricter adherence to data protection laws and a more responsible approach to managing consumer information. This section delves into specific legal violations and ethical concerns revealed by the incident.
3.1 Legal Violations
GDPR Breaches
The breach constitutes a clear violation of the General Data Protection Regulation (GDPR), which mandates robust safeguards for personal data. VW failed to implement encryption for sensitive data such as user names, email addresses, and precise geolocation. Furthermore, the company did not adhere to the principle of data minimization, which requires organizations to collect only the data necessary for operational purposes. By storing excessive data like user IDs and vehicle geolocations, VW amplified the privacy risks faced by its customers.
Failure to Meet Terms of Service
Another critical legal lapse involved the mismanagement of Amazon Web Services (AWS) credentials. Active credentials were stored in unprotected heap dumps,
exposing sensitive backend systems to unauthorized access. This breach of internal terms of service not only violated VW’s own data governance policies but also demonstrated a lack of due diligence in managing cloud-based infrastructure.
Regulatory Compliance
The incident also raises questions about compliance with broader regulatory requirements. For example, European Union (EU) vehicle data sharing regulations mandate the collection and sharing of specific data, such as crash alerts, to enhance road safety. However, VW’s overcollection of data far exceeded these requirements, collecting precise geolocation and user activity data unrelated to mandated safety purposes.
3.2 Ethical Concerns
Overcollection of Data
The breach revealed that VW collected data beyond what was operationally necessary, including precise geolocation, driver routines, and detailed user identifiers. Ethical data management practices emphasize proportionality, suggesting that organizations should limit data collection to what is essential. VW’s overreach not only violated consumer expectations but also increased the potential for misuses.
Privacy Invasion Risks
The collection of location data with high accuracy, down to 10 centimeters, poses significant privacy invasion risks. Such data can reveal sensitive details about
individuals’ routines, including places of residence, work locations, and personal habits. This level of granularity raises ethical concerns about the potential misuse of information and the lack of transparency regarding its collection.
Erosion of Consumer Trust
Incidents like the VW breach erode consumer trust in organizations’ ability to safeguard their data. Trust is a cornerstone of adopting connected technologies like electric vehicles (EVs). The incident reinforces public skepticism, with surveys indicating that only a minority of consumers trust automakers to handle their data responsibly. This erosion of trust could significantly hinder the adoption of EVs and other data-driven innovations.
4. Broader Implications
The Volkswagen (VW) data breach serves as a poignant example of how lapses in cybersecurity can have cascading effects, not only on the affected organization but
also on broader technological adoption and public trust. This section explores the multifaceted implications of such breaches, focusing on their impact on electric vehicle (EV) adoption, economic and reputational damage, and lessons drawn from other high-profile cases.
4.1 Impact on EV Adoption
Privacy Concerns Slowing Connected Car Adoption
The exposure of sensitive data such as precise geolocation and user activity information underscores the vulnerabilities inherent in connected car ecosystems. Privacy concerns among consumers are heightened when automakers fail to protect such critical data. Surveys reveal that only a small percentage of consumers trust automakers to handle their data responsibly, with incidents like the VW breach further eroding confidence. This mistrust could lead to slower adoption of EVs, especially in regions where data privacy is a key concern.
Trust Deficit in Automakers’ Data Security Capabilities
The breach amplifies skepticism about automakers’ ability to implement robust cybersecurity measures. This trust deficit poses a significant barrier to the widespread adoption of EVs and connected technologies, as consumers may hesitate to embrace innovations that compromise their privacy. Automakers must address these concerns proactively to sustain the momentum of technological advancements in the automotive industry.
4.2 Economic and Reputational Damage
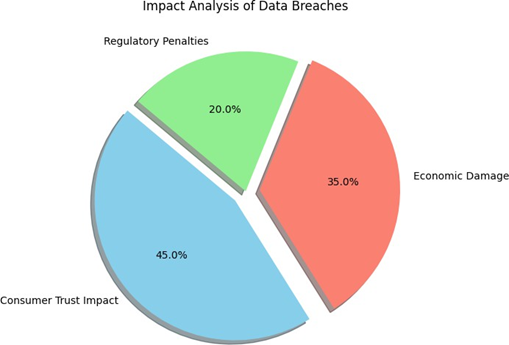
Potential Lawsuits and Regulatory Fines
Incidents like the VW data breach expose organizations to severe financial liabilities, including regulatory fines under laws like GDPR. Penalties for non-compliance with data protection regulations can be substantial, as seen in Meta’s $1.3 billion fine for GDPR violations. VW’s mismanagement of sensitive data not only invites potential lawsuits from affected consumers but also exposes the company to fines for its failure to meet regulatory standards.
Damage to VW’s Brand Image
For a company already recovering from the Dieselgate emissions scandal, the data breach compounds challenges to its reputation. VW’s brand image, especially in the EV market, is further tarnished by this incident, which undermines consumer
confidence in its digital offerings. Such reputational damage could hinder its efforts to position itself as a leader in sustainable mobility.
4.3 Lessons from Other Cases
Meta’s GDPR Fine for Data Transfer Violations
Meta’s $1.3 billion GDPR fine serves as a cautionary tale about the importance of adhering to data protection regulations. The fine highlights the consequences of failing to implement adequate safeguards for cross-border data transfers, underscoring the need for automakers like VW to prioritize compliance.
Equifax Breach: Failure to Patch Known Vulnerabilities
The 2017 Equifax breach, which exposed the personal data of nearly 150 million people, illustrates the catastrophic consequences of neglecting basic cybersecurity measures. A failure to patch known vulnerabilities resulted in a $575 million settlement, signaling the importance of regular security updates and proactive risk management. VW’s failure to secure its AWS credentials similarly reflects a lack of diligence in addressing known risks, emphasizing the need for robust internal security protocols.
5 Preventive Measures
Implementing robust preventive measures is essential to mitigate the risk of data breaches and enhance cybersecurity resilience. Technical safeguards, such as encryption of sensitive data both in transit and at rest, access controls with least- privilege policies, and AI-driven monitoring for anomaly detection, play a critical role in securing data systems. Regular vulnerability assessments and penetration testing ensure proactive identification of potential weaknesses. On the legal front, adherence to regulations like GDPR and clear communication of data collection practices build
trust and accountability. Ethically, organizations must limit data collection to essential information and conduct periodic reviews of retention policies to minimize unnecessary risks. These measures collectively create a strong defense against evolving cyber threats while fostering consumer trust.
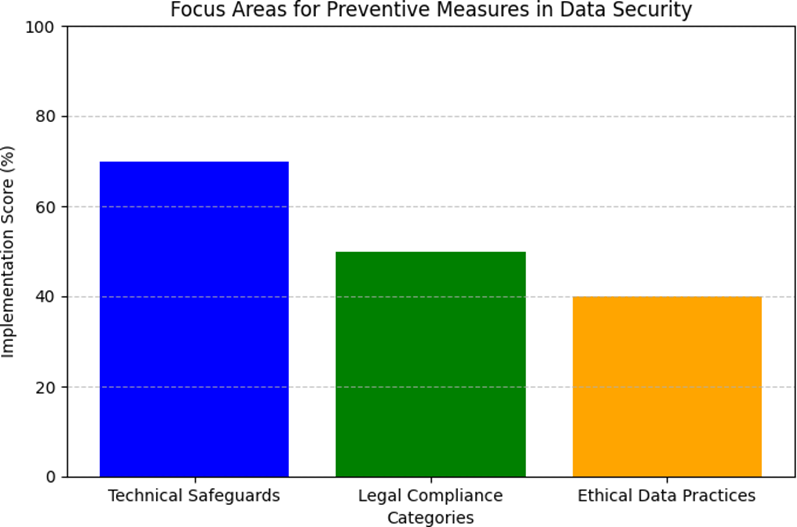
5.1 Technical Safeguards
To mitigate the risk of data breaches and enhance security frameworks, robust technical measures are essential.
- Encryption:
Encrypting sensitive information both during transit and storage is critical. This ensures that even if data is intercepted or accessed, it remains unreadable to unauthorized individuals. Advanced encryption protocols, such as AES- 256, should be employed for safeguarding data assets.
- Access Controls:
Enforcing the principle of least privilege (PoLP) ensures that access to sensitive systems, such as AWS credentials, is restricted to only those who absolutely require it. Routine audits, coupled with periodic rotation of access tokens, further minimize the potential for misuse or unauthorized access.
- Monitoring and Alerting:
Employing artificial intelligence (AI)-driven tools to monitor data access patterns allows for the detection of anomalies in real-time. This proactive approach can identify and mitigate potential breaches before they escalate.
- Regular Testing:
Conducting periodic penetration testing and vulnerability assessments is crucial for identifying and addressing security weaknesses. These practices simulate potential attacks, enabling organizations to rectify vulnerabilities in a controlled environment.
5.2 Legal and Compliance Frameworks
To ensure adherence to regulatory requirements and foster user trust, comprehensive legal and compliance strategies are necessary.
- Data Protection Policies:
Organizations must strictly comply with regional and global regulations, such as GDPR and CCPA. These frameworks mandate robust data protection measures and provide guidelines for transparent data handling practices.
- Transparency:
Establishing clear communication channels about data collection and usage practices builds trust with users. Transparent policies allow individuals to make informed decisions regarding their data.
- Third-Party Audits:
Independent evaluations of cloud and storage security configurations are essential for identifying potential vulnerabilities. Regular audits by third-party experts help organizations align with best practices and maintain regulatory compliance.
5.3 Ethical Data Collection
Ethical considerations are fundamental to maintaining user trust and ensuring data is handled responsibly.
- Minimization:
Organizations should limit data collection to information that is strictly necessary for operational purposes. For example, while battery health metrics are essential for EVs, detailed geolocation data may not be required and can pose significant privacy risks if collected unnecessarily.
- Retention Policies:
Data retention policies should be periodically reviewed to ensure alignment with current business needs and regulatory requirements. Outdated or redundant data should be securely deleted to reduce the risk of exposure in case of a breach.
6. Recommendations in the Context of Cyber Law in India
The Volkswagen data breach highlights critical vulnerabilities in data security, emphasizing the need for stringent adherence to cyber laws. In the Indian context, the following recommendations align with existing legal frameworks and emphasize the enhancement of organizational data protection practices:
6.1 Compliance with the Information Technology Act, 2000
- Adherence to Section 43A: Organizations must implement reasonable security practices to protect sensitive personal data. Non-compliance can lead to compensation for damages under Indian law.
- Certification of Security Standards: Companies should align with internationally recognized security frameworks like ISO 27001 to demonstrate compliance with “reasonable security practices and procedures.”
- Adherence to Data Localization Requirements: If applicable, ensure compliance with the Data Protection Bill provisions that may mandate data storage within India’s jurisdiction for critical personal data.
6.2. Strengthening Data Protection Practices
- Encryption Mandates: Organizations must employ robust encryption techniques, such as AES-256, for storing sensitive data in compliance with Section 72A of the IT Act, which penalizes unauthorized disclosure of information.
- Access Control Measures: Implement role-based access controls (RBAC) to limit unauthorized access to sensitive information, including cloud storage credentials and databases.
- Regular Audits and Incident Reporting: Conduct periodic IT audits and implement real-time breach reporting mechanisms to ensure compliance with Section 79 and CERT-In guidelines.
6.3. Adherence to GDPR-Equivalent Standards
While India is drafting its Data Protection Bill, companies should voluntarily align with GDPR-equivalent standards:
- Data Minimization: Collect only essential data and retain it for the minimum period necessary.
- Explicit Consent: Obtain clear and unambiguous user consent for data collection and processing.
- Data Protection Officer (DPO): Appoint a DPO to oversee compliance with data protection laws and respond to grievances.
6.4. Legal Repercussions for Non-Compliance
- Penalties for Data Breaches: Emphasize the penalties under Section 43A and Section 66 of the IT Act for negligence and unauthorized access to sensitive personal information.
- Liability for Misuse: Companies must ensure that their terms of service and privacy policies explicitly address liabilities arising from misuse of sensitive data by third parties.
6.5. Building Consumer Trust
- Transparency in Data Handling: Provide clear, accessible privacy policies to users detailing how their data will be collected, stored, and processed.
- Redressal Mechanisms: Establish efficient grievance redressal systems to address consumer complaints swiftly and ensure compliance with the IT Rules, 2011.
6.6. Cybersecurity Capacity Building
- Training and Awareness: Conduct regular training for employees on cybersecurity practices and India’s legal requirements.
- Ethical Hacking Initiatives: Collaborate with ethical hackers to identify vulnerabilities in IT systems proactively.
6.7 Recommendations for Policy Enhancements
- Inclusion of Specific EV Data Guidelines: The Indian government should consider enacting specific guidelines for data generated by connected vehicles, similar to EU directives.
- Mandatory Breach Notification: Enforce mandatory breach reporting requirements within a specified timeframe to ensure swift action and regulatory oversight.

7. Conclusion
The Volkswagen data breach is a stark reminder of the pressing need for robust cybersecurity measures and ethical data management in an increasingly interconnected world. The incident not only revealed significant legal and ethical lapses but also underscored broader implications for consumer trust, technological adoption, and corporate accountability. By failing to adhere to GDPR requirements and ethical data practices, Volkswagen compromised sensitive consumer information, highlighting vulnerabilities in connected car ecosystems.
As organizations navigate the complexities of data-driven innovation, the lessons from this breach emphasize the importance of embedding privacy-by-design principles, investing in state-of-the-art security measures, and fostering transparency in data practices. Companies must recognize that consumer trust is a critical enabler
of technological progress. Building resilient systems that prioritize data protection will not only mitigate financial and reputational risks but also serve as a foundation for sustainable innovation in connected technologies.
To move forward, organizations must adopt a proactive approach to cybersecurity, draw on lessons from high-profile cases, and engage with evolving regulatory frameworks to ensure compliance. The Volkswagen breach should act as a catalyst for industry-wide introspection and a commitment to safeguarding the digital ecosystem.
References
- GDPR Compliance Overview (https://gdpr-info.eu/)
- Chaos Computer Club Reports on VW Breach (https://ccc.de)
- Data Privacy Challenges in Connected Vehicles (https://www.dataprivacy.com/connected-cars)
- Meta’s GDPR Fine for Data Transfer Violations (https://dataprotection.ie)
- Ethical Implications of Data Breaches (https://ethicsinaction.org)
- Technical Analysis of Cloud Security Failures (https://cloudsecurityalliance.org)
- Chaos Computer Club Report (https://ccc.de)
- GDPR and Connected Vehicle Security (https://www.dataprotection.com/connected- cars)
- Volkswagen Data Breach Overview (https://spiegel.de)
- Ethical and Legal Implications of Data Retention (https://ethicsinaction.org)
- Cloud Security Misconfigurations in Automotive Industry (https://cloudsecurityalliance.org)
- GDPR Compliance Guidelines (https://gdpr-info.eu/)
- Chaos Computer Club Analysis of VW Breach (https://ccc.de)
- AWS Cloud Security Best Practices (https://aws.amazon.com/security)
- EU Vehicle Data Regulations (https://europa.eu/transport/road-safety/data-regulation)
- Data Minimization Principles (https://privacyinternational.org)
- Connected Vehicle Privacy Concerns (https://dataprotection.com/connected-cars)
- Ethical Data Collection Standards (https://ethicsinaction.org)
- Deloitte Consumer Data Trust Survey (https://deloitte.com/consumer-trust-survey)
- Automotive Industry Data Security Analysis (https://cloudsecurityalliance.org)
- Deloitte Consumer Trust Survey (https://www2.deloitte.com)
- Automotive Cybersecurity Reports (https://automotivecybersecurity.com)
- Connected Vehicle Data Security Insights (https://dataprotection.com/connected-cars)
- Privacy Concerns in EV Adoption (https://privacyinternational.org)
- GDPR Fines and Penalties (https://gdpr-info.eu)
- Meta’s GDPR Fine Analysis (https://dataprotection.ie)
- Impact of Dieselgate on VW (https://spiegel.de)
- Cybersecurity in Automotive Industry (https://cloudsecurityalliance.org)
- Lessons from Meta Data Breach (https://techcrunch.com/meta-gdpr-fine)
- Equifax Breach Analysis (https://www.ftc.gov/equifax-breach)
- Cybersecurity Vulnerability Management (https://securitymetrics.com)